For all of our clients running Microsoft Internet Information Services 6 or higher, you may find that after installing your new certificate via the supplied .p7b file, some browsers report that the Digital Certificate was signed by an unknown / untrusted Certificate Authority. This is due to a Self-Signed Certificate present in the Windows 2003/2008 Certificate Store, and should be removed.
This is due to a known issue with IIS 6/7. To correct this, the following procedure has been provided.
Open the Certificate Store for the Local Computer:
1. From the Desktop of your IIS Server, click "Start", then "Run", type 'mmc' (without the quotes), and then click "OK".
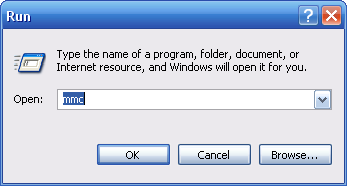
2. On the "File" menu, click "Add/Remove Snap-in" (See image below). A dialog box titled "Add/Remove Snap-in" will appear. Click the "Add" button. This will cause a window titled "Add Standalone Snap-in" to appear.
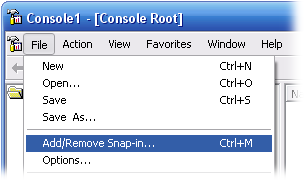
3. On the window titled "Add Standalone Snap-in", under "Snap-in", click "Certificates", then click the "Add" button at the bottom of the window.
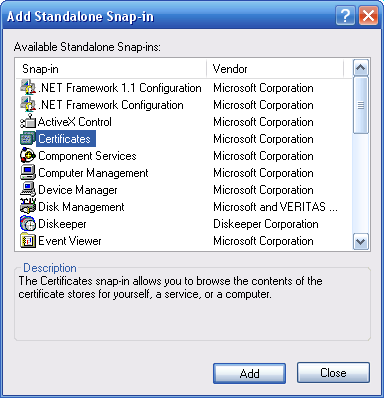
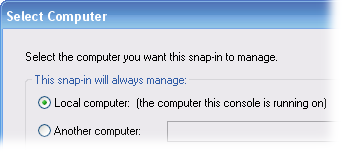
4. A window titled "Certificates snap-in" will open (see image below), asking you to choose which certificates to manage. Click the radio button next to "Computer account" (the lower of the three options), and then click "Next". This will open a new window titled "Select Computer".
5. In the "Select Computer" window, click the radio button for "Local Computer" and then click "Finish". You will return to the "Add Standalone Snap-in" window.
6. Now to finish up the selections. On the "Add Standalone Snap-in" window, click the "Close" button. The "Add/Remove Snap-in" window should now have the "Certificates (Local Computer)" snap-in added to it. Click the "OK" button at the bottom of the window.
Remove the SecureTrustCA certificate:
1. In the left-hand pane, click on "Certificates (Local Computer)", then click on "Trusted Root Certification Authorities", and finally then click on "Certificates".
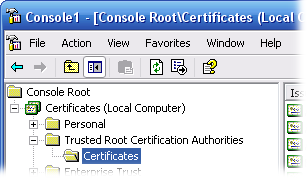
2. On the right-hand pane, scroll down till you see a Certificate that has been Issued To: and Issued By: "SecureTrust CA". This is the Self-Signed CA Certificate that is susceptible to a known issue with IIS 6/7. There should be only one certificate.
3. Delete the certificate. You should receive a warning dialog box that states "This is a root certificate. Deleting this certificate will invalidate this CA. Are you certain you want to delete this certificate?".
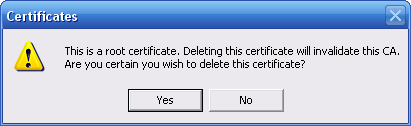
4. Click yes.
Now restart the website via the IIS Manager.
This error means that your browser is unable to authenticate your new VikingCloud™ certificate. There are two main causes for this error:
The most common cause is that your intermediate certificates aren't installed or may not be installed properly. These intermediate certificates explain to the browser that the certificate can be trusted. Once they're installed properly, the error will disappear. Please return to the corresponding installation procedures for your server and complete the installation.
The other cause may be that your VikingCloud certificate isn't fully installed. Many servers actually create a "self-signed" or temporary certificate when you first create your CSR and private key. WHM, Plesk, and Zeus are just a few examples of servers that do this. Sometimes this certificate isn't removed when you install the VikingCloud certificate. Verify that your actual VikingCloud certificate is installed rather than the self-signed certificate.
This means that your certificate is either expired or not yet valid when the dates on the certificate are compared to your local computer's clock. There's two main reasons this error may appear: Your certificate may actually be expired. If you log into the VikingCloud™ Control Center, your certificate's expiration date will appear there. If the expiration date has passed, don't worry - you can renew your certificate quite easily. You can renew it via the VikingCloud™ Control Center, or you can call us and we can take care of it over the phone instantly.
If the expiration date hasn't passed, double check your computer's clock. The clock might be set too far into the future. Synchronize your clock with a reliable time source, close your browser, and try accessing your site securely again.
This error means that the web address on the certificate itself doesn't match the address in the address bar of your browser.
For example, if you install a certificate on your site for www.domain.com and you access your site as https://domain.com, your browser cannot match the names. Unfortunately, www.domain.com is not the same as domain.com. Please remember this in your check-out scripts.
This can also occur if the IP addresses on the server aren't properly configured. You could be accessing someone else's digital certificate on your server when you attempt to access your site. Check with your web hosting provider if you think this might be the case.
This error means that you have items with absolute paths to an insecure source on your secure pages. For example, if you have an image tag on a secure page that looks like this, you will receive an error:
<img src="http://www.domain.com/images/image.jpg">
Instead, use a relative link so that your images can be accessed insecurely or securely, depending on where the customer is on your site:
<img src="/images/image.jpg">
Another possible cause would be a third-party's script over an insecure source. An example of this would be:
<script src="http://www.not_your_domain.com/script.js" type="text/javascript">
Most often, a provider of such scripting services will also provide a secure means of accessing them. For example:
<script src="https://ssl.not_your_domain.com/script.js" type="text/javascript">